Today I’m writing a guide on how to configure ClearPass to allow management of Cisco IOS switches with TACACS+. Please note that to perform TACACS+ enforcement ClearPass requires an Endpoint license be upgraded to a Access license.
First we apply the following configuration on the Cisco switch. This was tested with IOS-XE but any recent-ish IOS should be fine.
aaa new-model
!
tacacs server CLEARPASS01
address ipv4 <IP ADDRESS>
key 0 <KEY>
!
aaa group server tacacs+ CLEARPASS-TACACS
server name CLEARPASS01
ip tacacs source-interface vlan 99
!
aaa authentication login default group CLEARPASS-TACACS local
aaa authentication enable default group CLEARPASS-TACACS enable
aaa authorization exec default group CLEARPASS-TACACS local if-authenticated
In my ClearPass lab I am using the AD authentication source and Device Groups that have been previously configured in my guides. Please note that the TACACS server key needs to be entered into the Network Devices section in ClearPass. This will not be covered in this guide as it was pre-configured as part of the Device Group.
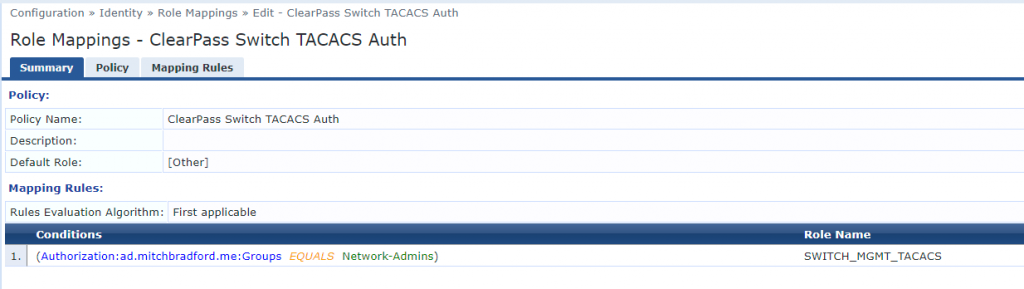
We will start by creating a Role and Role Mapping Policy. This is as simple as going to Identity > Roles > Add and creating one called SWITCH_MGMT_TACACS. We then create a Role Mapping Policy by going to Identity > Role Mappings > Add and configure the following settings:
- Policy Name: ClearPass Switch TACACS Auth
- Default Role: [Other]
- Conditions: (Authorization:ad.mitchbradford.me:Groups EQUALS Network-Admins)
- Role Name: SWITCH_MGMT_TACACS
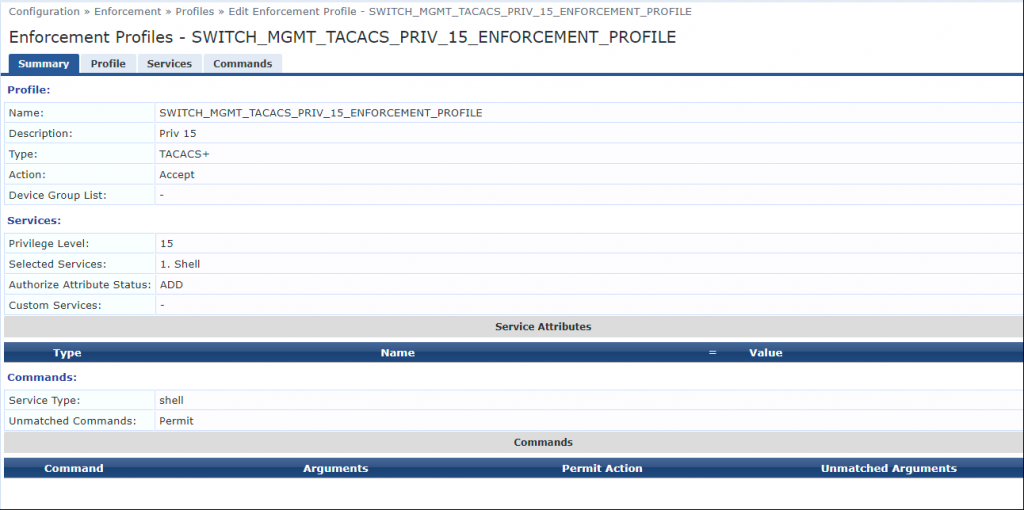
Next we create an Enforcement Profile by going to Enforcement > Profiles > Add and using the following settings:
- Name: SWITCH_MGMT_TACACS_PRIV_15_ENFORCEMENT_PROFILE
- Type: TACACS+
- Action: Accept
- Privilege Level: 15
- Selected Services: Shell
- Service Type: Shell
- Unmatched Commands: Permit
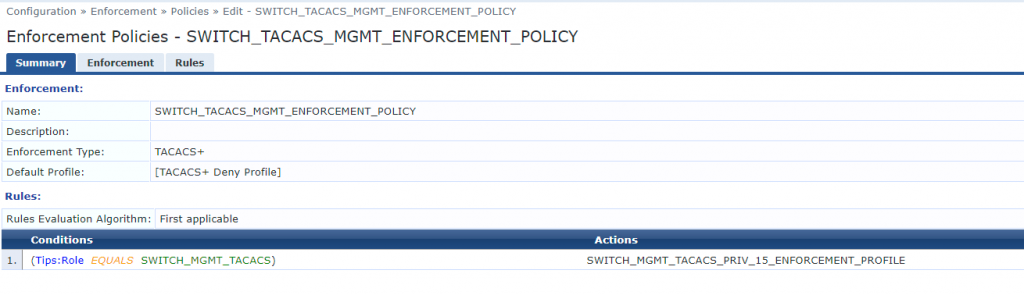
We will now create an Enforcement Policy by going Enforcement > Policy > Add and using the following settings:
- Name: SWITCH_TACACS_MGMT_ENFORCEMENT_POLICY
- Enforcement Type: TACACS+
- Default Profile: [TACACS+ Deny Profile]
- Conditions: Tips:Role EQUALS SWITCH_MGMT__TACACS
- Actions: SWITCH_MGMT_TACACS_PRIV_15_ENFORCEMENT_PROFILE
And finally to tie it all together we create the Service by going Services > Add and use the following configuration:
- Name: CISCO_SWITCH_TACACS_MGMT
- Type: TACACS+ Enforcement
- Status: Enabled
- Match ALL
- Connection NAD-IP-Address BELONGS_TO_GROUP Switches
- Connection Protocol EQUALS TACACS
- Authentication Sources: ad.mitchbradford.me [Active Directory]
- Role Mapping Policy: ClearPass Switch TACACS Auth
- Enforcement Policy: SWITCH_TACACS_MGMT_ENFORCEMENT_POLICY
Now that all this configuration is tied together with an active service, you should be able to see TACACS+ requests being processed by ClearPass by checking the Access Tracker under Monitoring > Access Tracker.
