In this post I will go through the process I used to test ClearPass Profiling on endpoints and passing through the endpoints VLAN to a colourless port on a Cisco switch.
First we’ll go through the configuration on the Cisco IOS side of things.
RADIUS Configuration:
aaa new-model
radius server dot1x-auth1 <key>
address ipv4 <CPPM SERVER> auth-port 1812 acct-port 1813
timeout 2
retransmit 1
key 7
aaa group server radius dot1x-auth
server name dot1x-auth1
aaa authentication dot1x default group dot1x-auth
aaa accounting dot1x default start-stop group dot1x-auth
aaa authorization network default group dot1x-auth
dot1x system-auth-control
On the port(s) you’d like configured as colourless ports, place the following configuration:
Interface x/x/x
switchport mode access
switchport access vlan <Provisioning VLAN>
authentication port-control auto
dot1x pae authenticator (Remove this if you don't want 802.1x and just MAB)
Mab (Remove this if you don't want MAB)
Note: dot1x pae authenticator command lists the interface as a 801.x enabled interface. It is mandatory if you want to run 802.1x
VLAN Configuration
With ClearPass we want to reference the VLAN name and not the VLAN ID so we are able to support multiple switches that may have different VLAN IDs for the same purpose. In my example I have the following:
VLAN Name Status Ports
1 default active Gi1/0/4, Gi1/0/5, Gi1/0/6
10 VLAN0010 active Gi1/0/1
20 VLAN0020 active Gi1/0/12, Gi1/0/13, Gi1/0/14
30 VLAN0030 active
50 VLAN0050 active Gi1/0/2
99 VLAN0099 active Gi1/0/7
As we are doing profiling of the endpoints, we also require a dhcp ip helper-address pointing to the ClearPass server.
ClearPass Configuration
First you will need the Network Device configured in ClearPass with a key matching what was configured earlier on the Cisco switch. You can configure this by going Configuration > Network > Devices and creating the device there. The RADIUS Shared Secret is the key you want matching on ClearPass and the Cisco switch. If it’s not automatically ticked, please ensure the Enable RADIUS Dynamic Authorization is ticked with the default port of 3799. As an alternative you can also just add your entire management subnet here.
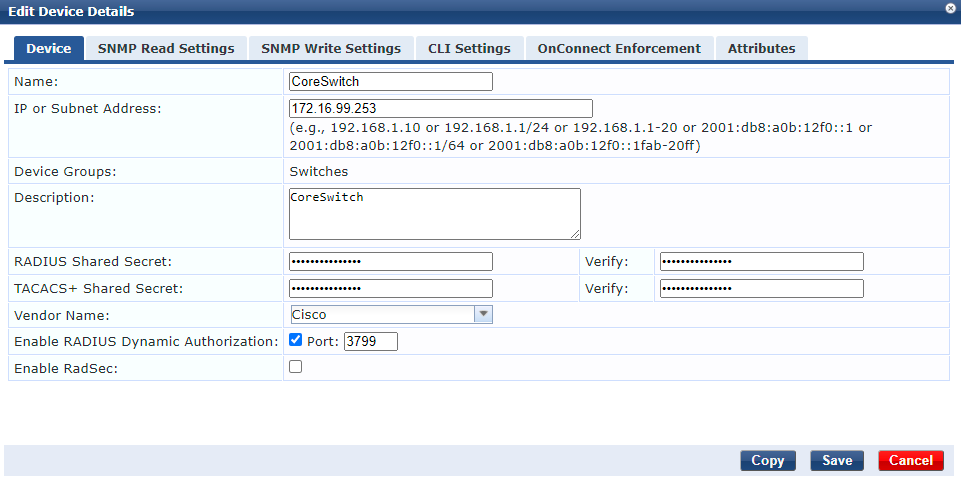
Next we will create a role for each endpoint type we are profiling, in my example I am only profiling an Aruba AP because it’s what I have quick access to. Go to Configuration > Identity > Roles and create a role for this endpoint type.
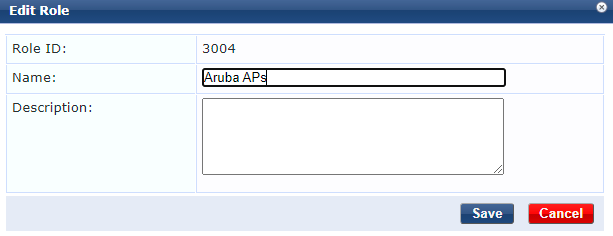
We will now create the Role Mapping by going to Configuration > Identity > Role Mappings. I’m just mapping devices in the Endpoint Repository that match the category of Access Points to the Role of Aruba APs. This would obviously need a bit more tightening up like matching Vendor as well if you also have a different vendors APs available.
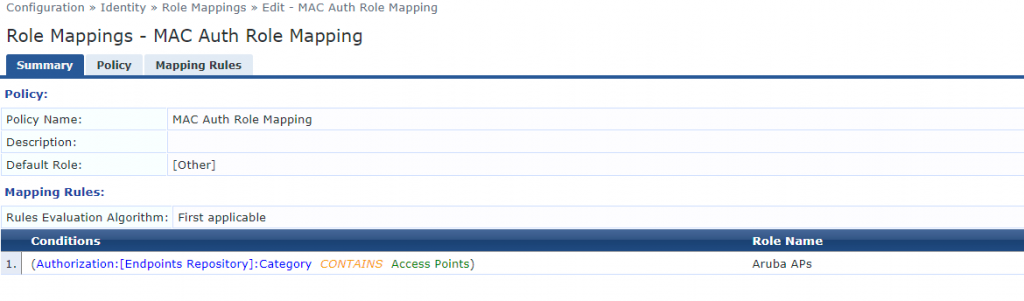
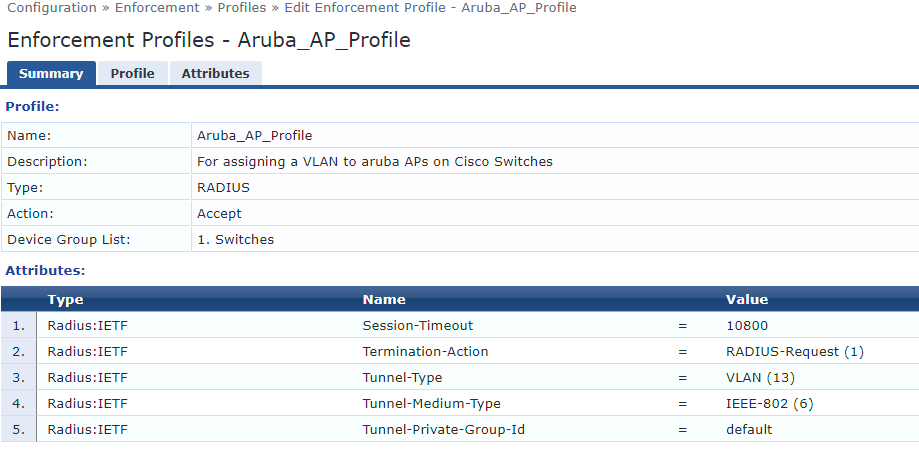
Next we create an Enforcement Profile. This is where we specify what VLAN the endpoint should be on. In my example with Cisco switches the Radius:IETF type was sufficient. In theory it should be OK across other vendors, but if you get stuck you can reference the Aruba ClearPass Wired Policy Enforcement Solution Guide for more assistance. To create this Enforcement Profile we go to Configuration > Enforcement > Profiles. I will reiterate here that we want to match the Tunnel-Private-Group-Id to the VLAN Name on the switch. This helps us have the same profile work across multiple sites that may have different VLAN IDs for similar VLANs.
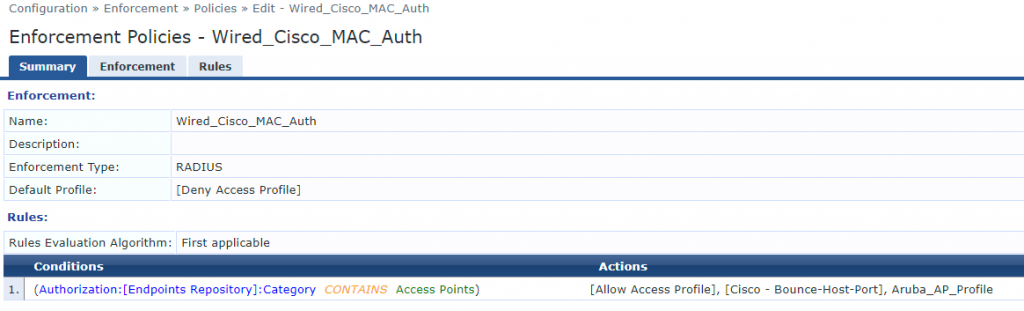
We now create an Enforcement Policy so we can tie together the actions and Enforcement Profiles each device should have. This can be configured by going to Configuration > Enforcement > Policies. In my example I am telling the port to bounce because it’ll change VLANs and to assign the Enforcement Profile we created in the previous step which specified the VLAN Name. If you’d like to find other identifying factors to match on, you can view the device MAC Auth by going to Monitoring > Access Tracker.
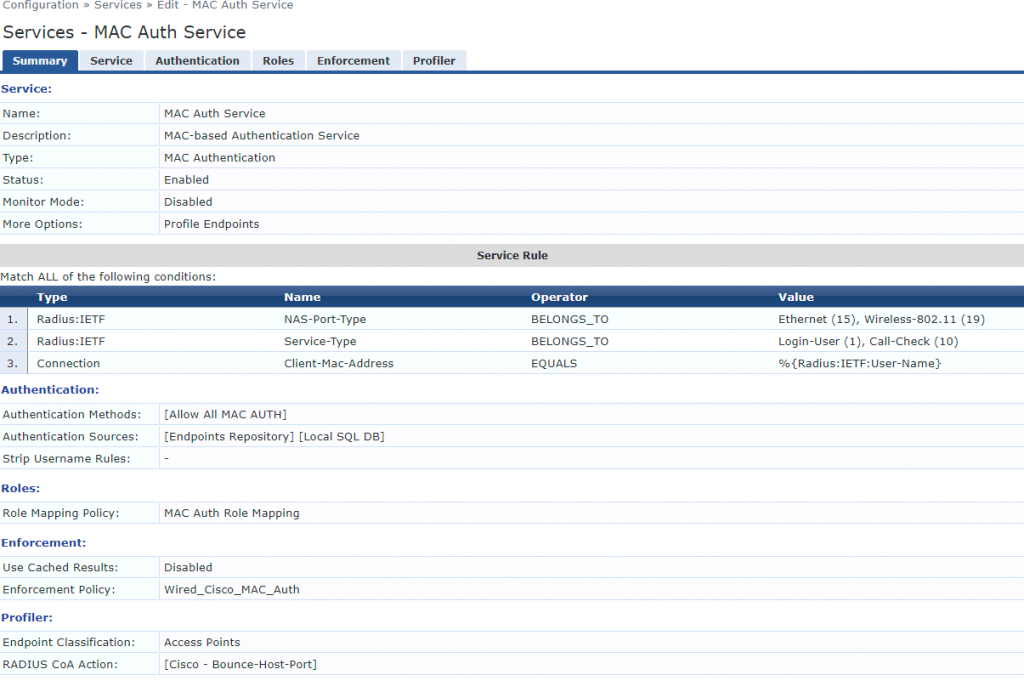
And finally we create a Service to tie these all together by going to Configuration > Services. In my example I’m matching on wired and wireless clients as it’s a lab, however, if you’re purely doing MAC Auth for wired and want to break Guest wireless out onto it’s own Service like I recommend, I’d remove the Wireless-802.11 value in the Service Rules. As we are profiling endpoints it’s important to tick Profile Endpoints under the Service tab. Under profiler I also selected Access Points under Endpoint Classification and told ClearPass to instruct a port bounce here as well, to ensure the endpoint is placed on the correct VLAN.
If you manually bounce the port you should now be able to run show mac address-table interface gigabitethernet x/x/x and see the VLAN the port is operating on. You can also see the profiled device by going to Configuration > Identity > Endpoints.
