In this guide I’m going to try and use the default roles wherever possible, as authenticating the HTTPS management of ClearPass against Active Directory is a fairly straightforward process. As a note, I’ve covered configuring Active Directory as an Authentication Source in a previous guide, so I won’t include it here.
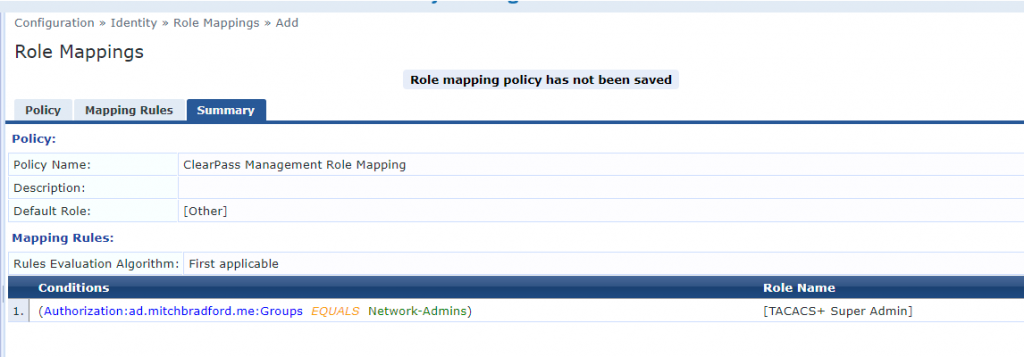
First we create a new Role Mapping with the following settings:
- Policy Name – ClearPass Management Role Mapping
- Default Role – [Other]
- Conditions
- (Authorization:<ad source>:Groups EQUALS <OU Group>)
- Role Name: [TACACS+ Super Admin]
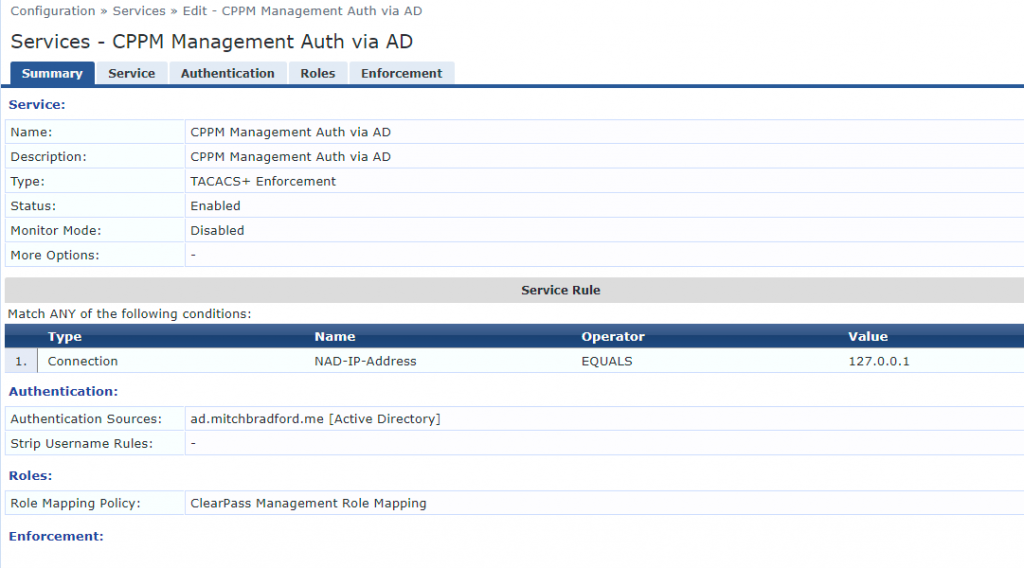
We now create a new service to tell ClearPass where to apply everything
- Name – CPPM Management Auth via AD
- Type – TACACS+ Enforcement
- Connection NAD-IP-Address EQUALS 127.0.0.1
- Authentication Sources: <AD Source>
- Role Mapping Policy: ClearPass Management Role Mapping
You can now test logging in with a different web browser and follow the auth process in access tracker.
